In the dynamic landscape of today’s interconnected world, ensuring the security of our digital and physical environments has become paramount. The concept of Total Control has emerged as a comprehensive approach to managing security ecosystems, leveraging the latest systems and technologies. Total Control entails the seamless integration of various security measures, from advanced surveillance systems to robust cybersecurity protocols, to create a unified and responsive defense mechanism. At its core, Total Control is about proactive monitoring, rapid response, and adaptive resilience. In the realm of physical security, cutting-edge surveillance systems equipped with artificial intelligence AI and machine learning algorithms enable real-time threat detection and identification. These systems not only act as a deterrent but also provide invaluable data for post-event analysis. Complementing this, cybersecurity measures play a pivotal role in safeguarding digital assets. Advanced firewalls, intrusion detection and prevention systems, and encryption technologies collectively fortify the digital perimeter.
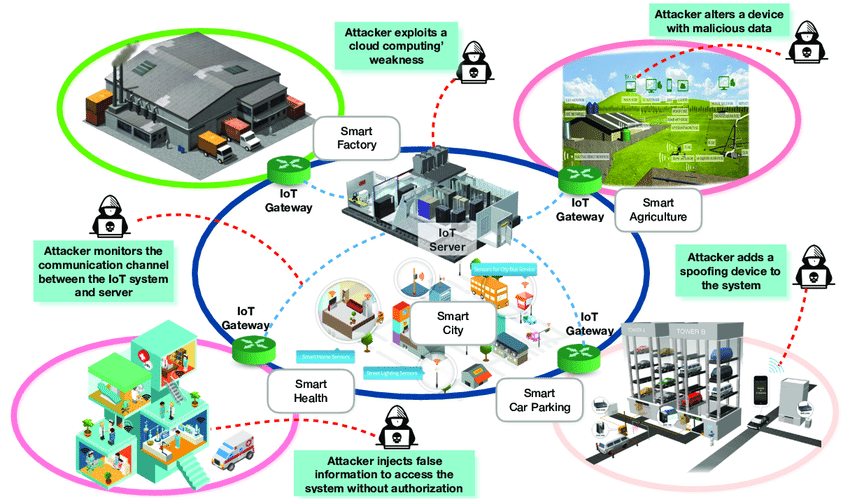
Total Control extends beyond traditional silos, fostering collaboration among different security components to create a synergistic defense mechanism. Centralized command and control centers, equipped with state-of-the-art dashboards and analytics tools, empower security personnel to make informed decisions swiftly. The integration of automation and smart technologies further enhances response times, as systems can autonomously initiate predefined actions in the face of security breaches. The ability to remotely monitor and control security systems through mobile applications adds an additional layer of flexibility and responsiveness. As the Internet of Things IoT continues to proliferate, Total Control adapts to encompass a wide array of connected devices, from smart sensors to interconnected access control systems. This holistic approach not only fortifies traditional security perimeters but also addresses vulnerabilities that may arise from the expanding attack surface presented by the IoT.
Moreover, Total Control embraces continuous improvement through data analytics and feedback loops. Security incidents and their resolutions are meticulously analyzed to identify patterns, enhance predictive capabilities, and optimize resource allocation and visit the site. This data-driven approach not only strengthens the security posture but also ensures a more cost-effective and efficient use of resources. In an era where threats are multifaceted and ever-evolving, Total Control is not a one-size-fits-all solution. Instead, it is a dynamic and adaptive framework that evolves with technological advancements and emerging threats. Collaboration between security experts, technology developers, and policymakers is crucial to staying ahead of the curve. Furthermore, education and awareness programs play a vital role in empowering individuals and organizations to contribute to the overall security ecosystem. As we navigate the complexities of an interconnected world, Total Control emerges as a beacon of resilience, offering a comprehensive and integrative strategy to manage and mitigate security risks across physical and digital domains.




